BRING YOUR OWN DEVICE

What options allow you to use your personal device to access work resoucrces
For companies that don’t want the expense of purchasing company managed phones they can allow access to the companies’ resources on personally owned devices. With Android devices you can achieve a BYOD device strategy by having a Work Profile and with IOS you can achieve a similar solution using a MAM Profile (mobile app management profile). Both options allow for the centralised management of the devices, Compliance policies and policy implementation to protect and control device security on the work side of the device. In addition, they will allow for the provisioning of Company resources they can range from email, teams, application created for specific tasks, jobs and document management.
What is Android work profile?
Bring your own Device (BYOD) is when an employee uses their own device to enrol in the company’s UEM (Unified Endpoint Management) solution, once enrolled it will create a separate container called a Work Profile on the phone.
This allows the employee to use one phone without IT having access to their personal data on the device. The work profile side is controlled fully by IT and is encrypted with a UEM defined encryption profile. IT has full control of the apps, restrictions, and information within the work profile including but not limited to VPN, WI-FI, Certificates and other security controls. The personal side of the device is not corporately managed allowing the use a personally enabled experience. There is an also an option to allow the phone app to read the contacts from the work profile, which is important when calls are incoming, also meaning you don’t have to mix your personal and work contacts.
|
|
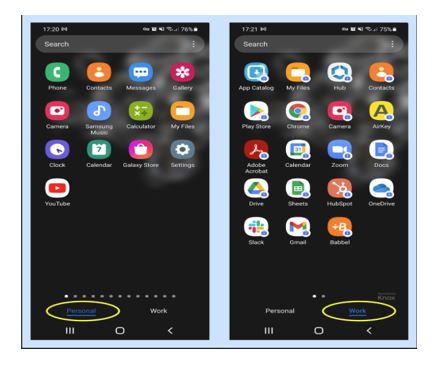
In this picture the left side is the personal side and on the right is the work profile – the work profile apps have blue locks on the app so there is no confusion what app you’re using. It will also indicate on the bottom which side you are on and when you unlock the device.
|
Data Control with work profile
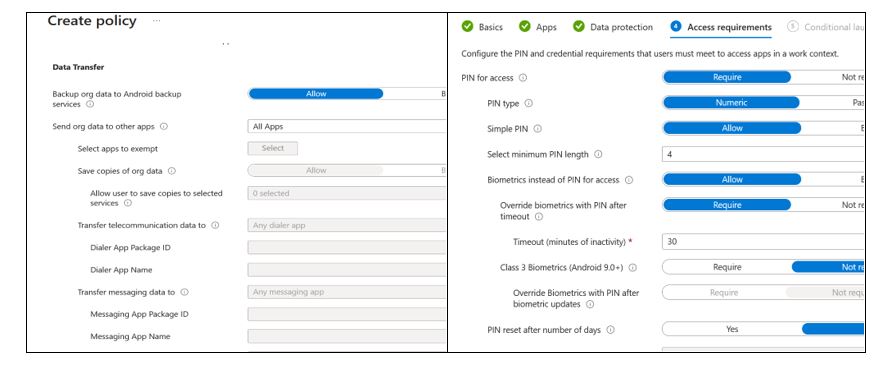
Android work profile data control policies allow IT to enforce policies, some examples are below
- Require a password for the work profile including the password length and complexity
- Disable data sharing between the work apps and the personally enabled side of the device
- Restricting copy and paste functions.
- Placing a restriction on the ability to screenshot
- Requiring encryption
- The work profile side can be wiped exclusively from the personal side of the device
What is MAM?
MAM (Mobile Application Management) is a security approach that focuses on managing and securing enterprise applications on mobile devices without requiring full device control. It allows IT administrators to control and protect corporate apps and data, even on personal (BYOD) devices, without affecting personal apps or data. This can be achieved using Intune app protection policies and conditional access policies. This allows Admins to control how the work apps are accessed, used and deployed.
These policies protect the organisations data from been shared or leaked and controls how the application is used. They also manage applications settings and versioning control allowing the organisation to keep apps up to date, conditional access controls allow access to applications based on location, user risk and device compliance. MAM does not provide the ability to manage the entire device, such as enforcing device-level encryption or remotely wiping the entire device.
Data control with MAM
App-level control: MAM focuses on controlling access to and usage of specific work apps with the use of policies.
- Restrict data sharing between managed apps and unmanaged apps.
- Encrypt work data within the app.
- Require app-specific PINs or authentication.
- Selectively wipe the work data within the app.
Advantages of BYOD and MAM
- Can protect companies’ data without the need to manage the device fully.
- Cost Savings on hardware and maintenance for the organisation when BYOD is implemented and deployed correctly
- Only removes data from work profile\apps and doesn’t affect the personal data on the device.
- Employees don’t need to carry two phones and have freedom of choice with their personal model
- Data is secure and is completely encrypted
- Work profile and apps are separated in their own containers and does not get affected by personal data
- Remotely configuration of the work applications and profiles
- The organisation has the option to access detailed app usage, performance and optimise app management
- End users can make a personal decision on their Device and OS within the confines of the companies defined BYOD policies.
DisAdvantages of BYOD and MAM
- IT admins can’t remotely wipe phone if lost but BYOD uses encryption key management to keep work data safe and can send wipes to work side/ apps.
- BYOD must be configured correctly within an organisation to ensure there is not a security risk allowing data to be leaked
- With BYOD you will have a wide range of device models and Operating Systems, when issues arise, this setup can lead to longer time solving the issues due to the differences in systems and the solutions to fix the issue.
- Lack of uniformity with devices and older devices could cause risks and compatibility issues if not managed correctly.
- Increase in distraction as using personal device alongside work apps
- Higher risk of theft and lost devices with more usage
DisAdvantages of BYOD and MAM
- Personal devices may lack proper security controls, increasing the risk of malware, phishing, and data breaches.
- Without the proper controls Employees might accidentally or intentionally share sensitive business data via personal apps.
- Ensuring compliance with industry regulations (e.g., GDPR, HIPAA) can be harder on personal devices.
- Supporting various OS versions, manufacturers, and security features can complicate IT management.
- IT teams have limited visibility over personal devices compared to company-managed ones.
- Employees may feel uncomfortable with company policies on their personal devices, leading to resistance.
- Running enterprise security apps alongside personal apps may slow down devices and affect user experience
- Unlike MDM, MAM only manages apps, this may make it less effective for enforcing full security policies.
- Some enterprise apps may not support MAM policies, reducing effectiveness.
- Complex Deployment – Deploying and enforcing MAM policies across various platforms and devices can be challenging.
Conclusion
Implementing BYOD (Bring Your Own Device) and MAM (Mobile Application Management) can enhance workforce flexibility and productivity and provide cost savings to the organisation. But it also may introduce security, compliance, and management challenges. While BYOD allows employees to use personal devices for work, ensuring security without compromising user privacy requires a well-defined BYOD strategy. MAM helps mitigate security risks by managing enterprise applications rather than the entire device, making it a practical solution for protecting corporate data in BYOD environments.
However, successful implementation requires:
- A clear BYOD policy that defines security expectations and acceptable usage.
- Robust MAM solutions to enforce app-level security and prevent data leakage.
- Employee awareness and training on security best practices to reduce risks.
- Regular monitoring and policy updates to address evolving cyber threats.
While BYOD and MAM provide a balance between security and user convenience, organizations must carefully assess their risk tolerance, compliance requirements, and IT capabilities before adoption.