Securing Your Business Mobile Endpoints


Why you need to secure your Mobile Endpoints
Most organisations spend large amounts ensuring the security of their traditional IT infrastructure, however what can become overlooked is the small powerful device that most people use every day: the mobile device in their pocket.
Mobile device usage in business has grown substantially over the last number of years. Mobile devices (including Smartphones, Tablets and Laptops/MacBook’s) have become key business tools, securing the data both personal and business stored on these devices has become a cause for concern for both businesses and government departments.
The financial consequences of personal data being shared incorrectly are significant. The introduction of the GDPR regulations in Europe has focussed the minds of management in looking at ways of securing access to this data.
The Data Protection Commission report for 2021 showed an increase in queries and complaints of 7% compared to 2020. The DPC received a total of 6,549 valid breach notifications in 2021. (Source: https://www.dataprotection.ie/en/news-media/press-releases/data-protection-commission-publishes-2021)
While the larger breaches and fines always get the headlines the reputational damage and costs to rectify the data breach can sometimes be more impactful on a business.
The Data Protection has issued some basic guidance to help with data protection on mobile devices:
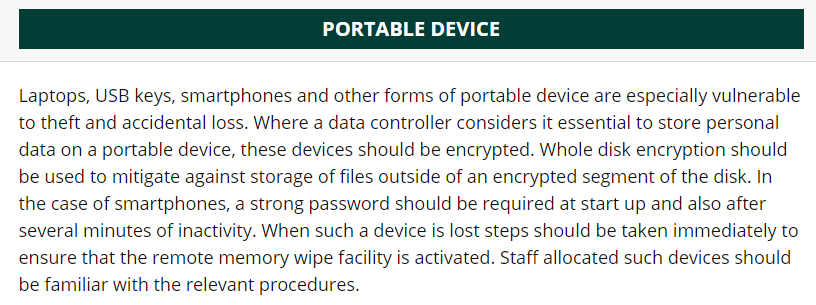
(Source: https://www.dataprotection.ie/en/organisations/know-your-obligations/data-security-guidance)
Enforcing these guidelines on Smartphones and tablets would be impossible without a properly configured UEM solution.
At the very least any business should have:
- Defined acceptable use policies for their corporate owned devices.
- A clear policy on BYOD (Bring Your Own Device) usage.
- A Unified Endpoint Management (formerly Mobile Device Management) solution in place.
A lot of entities are now looking beyond the Unified Endpoint Management (UEM) solutions and looking to add a Mobile Threat Detection solution to add additional security.
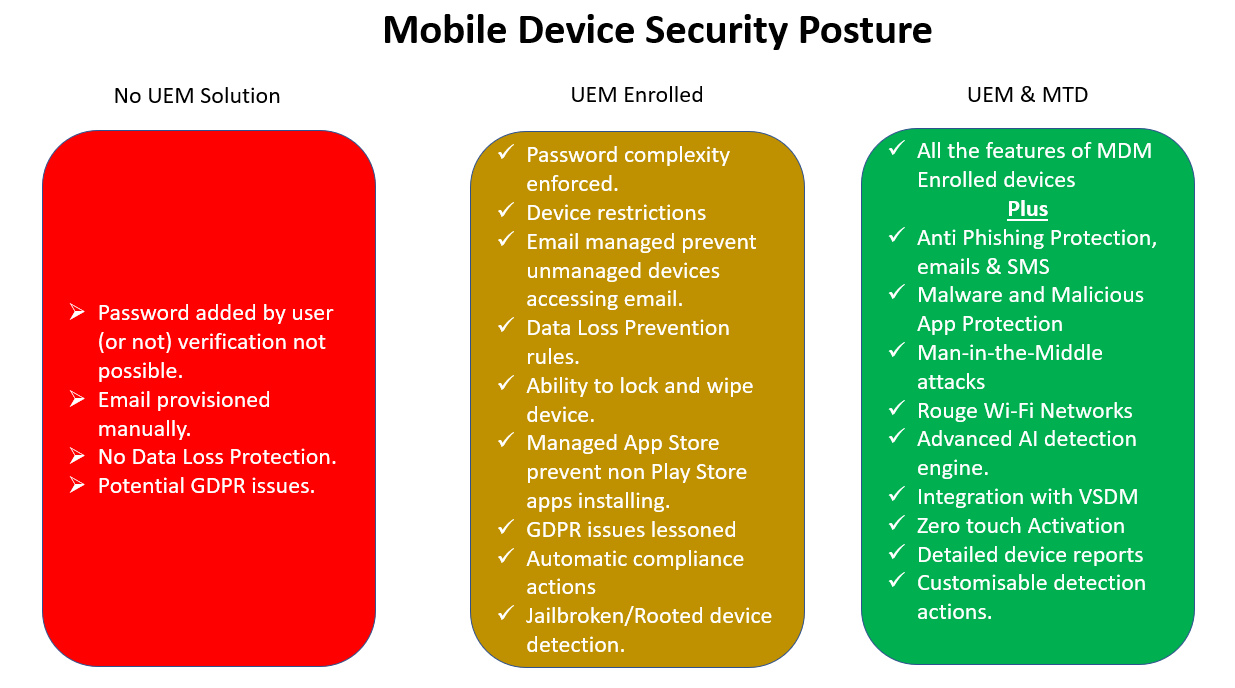
If we think of mobile security like a set of traffic lights, then:
- Having no UEM solution would be a red light.
- Having a properly configured UEM solution would be the amber light.
- Having both a properly configured UEM and MTD solution would be the green light.
How to choose the best Unified Endpoint Management solution?
The first steps to securing your mobile endpoints should be choosing the best UEM solution to meet your needs.
There are a large number of UEM solutions available right now and choosing the best one to meet your needs can be a daunting task.
As a basic checklist the items to check when evaluating a UEM solution, you should consider the following:
|
Item |
Reason |
|
Supported Devices |
You need to ensure that the solution can support your chosen device platforms.
|
|
On Premise v Cloud Hosted |
Your business may require the additional security of being installed on your network rather than a cloud hosted option. Some UEM’s may not provide an on-premise solution and will only offer a cloud hosted solution. If an on-premise solution environment is required remember to factor in items such as:
|
|
Support for new OS releases |
Check how new OS releases are supported. You don’t want to have to wait for a major update for the new features of your latest Android or iPhone to be supported. Some of the more established UEM’s like Omnissa’s Workspace ONE pride themselves on offering same day support for the latest updates. |
|
Automated enrollment |
The UEM should support the automated enrolment methods such as: Google Zero Touch Samsung Knox Mobile Enrollment Apple Device Enrollment Programme (Apple Business Manager) Microsoft Auto Pilot If it can’t support these technologies prepare for headaches enrolling devices in the future. |
|
Android Enterprise Support |
Google changed the management of Android devices in 2019 to Android Enterprise and insisted that all UEM’s support this enrolment method going forward. Even if currently you have no plans for Android devices in your estate, a UEM that does not support Android Enterprise should be a red flag. (There are specialist solutions for iOS and iPadOS devices but choosing one of these could result in having to change your UEM in the future should Android become part of your strategy) |
|
Flexibility |
Can you support different configurations for different use cases? For example single app mode or multi user devices. |
|
Capacity |
The chosen UEM must be able to grow to meet your business requirements as your business expands. |
|
Third Party Integrations |
Ensure that the chosen solution can integrate with any third party solutions you are deploying such as MTD. |
|
Cost |
Beware of hidden costs, most UEM’s will quote you for the basic service, but when you need to add additional services and configurations there may be a cost uplift. I have put cost here at the bottom of the list, cost should not override functionality when choosing your UEM solution. |
Some basic recommendations:
- Chose a well-established UEM solution. Stay away from new immature solutions or solutions that are built to support one OS type.
- Get management buy in. Senior management should not have the option to opt out of managing their device, the potential penalties for a data breech are too severe.
- When choosing a partner to implement your solution, ask for reference sites.
- You will not please everybody in your business, but remember data loss prevention policies are key to mitigating any GDPR issues. If that user can no longer use their favourite messaging application on their corporate device they will have to accept it for the good of the business.
- Know your device estate. If you only issue iPhones why are there Android devices accessing emails and can you prevent this with your chosen solution?
- Your chosen solution should be deployed on every corporate device or device with access to corporate data. You can’t half close the gate.
- Review your policies and configurations regularly and keep then in line with recommended policies from the device manufacturer.
Takeaways
- Unsecured mobile endpoints should be not exist in any business.
- Security must not be sacrificed for functionality.
- UEM and MTD provide the best mobile security posture.
- Can your business afford the potential fines under GDPR and the reputational damage of a breach?
- No business will ever be fully secure so constant vigilance and updating of security policies and procedures is required.
Author: Cathal Henry – Senior Solution Architect